This is How Hackers Stole 116 BTC From University of California
Hackers pulled off a successful ransomware attack on COVID-19 researchers from the University of California in San Francisco and received 116 bitcoins.
Now, recently surfaced transcripts reveal how the entire operation played out.
Phase One: The Hack
Although the name of the group was initially a mystery, the Bloomberg report said that the organization had a history of targeting health-care entities. Later on, a group dubbed Netwalker claimed credit for executing the ransomware attack on the University of California in San Francisco in early June.
The UCSF confirmed the attack specifying that the target was a research team testing a possible coronavirus vaccine. The university had alerted security experts and law enforcement agencies of the attack and that “with their assistance, we are conducting a thorough assessment of the incident, including a determination of what, if any, information may have been compromised.”

By executing a ransomware attack, the hackers gain control over sensitive information belonging to the victim and request some form of a ransom paid to unlock it. In this particular scenario, Netwalker initially demanded $3 million.
Phase Two: The Negotiations
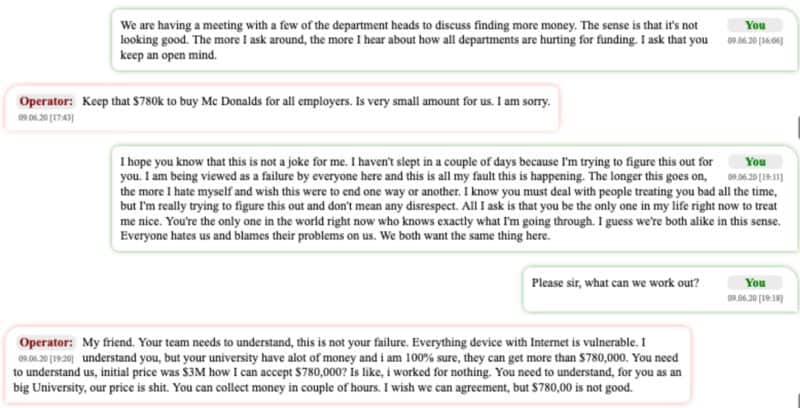
According to the transcripts revealed by Bloomberg, the UCSF negotiator entered the chatroom four days after the hack when the attackers had already locked down multiple servers used by the researchers.
The hackers redirected the UCSF negotiator to a webpage on the dark web containing at least ten victims and demands and a flashing red timer counting down to a payment deadline. As of June 5th, it read: 2 days, 23 hours, 0 minutes. If the ransom was not paid in that timeframe, the price would double.
Although the UCSF negotiator claimed that the university is down on funds due to the COVID-19 pandemic, the hackers’ representative, called the Operator, said that a school collecting more than $7 billion in revenue each year should have no issues paying a few million.
“You need to understand, for you, as a big university, our price is shit. You can collect that money in a couple of hours. You need to take us seriously. If we’ll release on our blog student records/data, I’m 100% sure you will lose more than our price what we ask.” – the Operator warned.
Phase Three: Pay With Bitcoin
The negotiations continued for almost a week with some classic strategies employed by the UCSF negotiator, like requesting a delay and trying to reduce the ransom price.
Ultimately, some of the tricks indeed worked as the two sides reached an agreement – 116 bitcoins. With the price of one BTC at just beneath $10,000 at the time, the value equaled 1.14 million in USD.
After a day and a half of clearing the deal and purchasing the bitcoins, the UCSF transferred the funds. Once they did, the university received access to the decryption key for the locked information, and the hackers forwarded all the data they had stolen. It took the attackers two days to decrypt, transmit, and show that they had deleted their copies of the stolen files, but the drama ended on June 14th.
The post This is How Hackers Stole 116 BTC From University of California appeared first on CryptoPotato.