The Fundamentals Of How Bitcoin Works
In part three of this four-part series, Eric Yakes takes us through the inner mechanisms of the Bitcoin network.
The Wall Street Analyst’s Intro to Bitcoin:
- The Dimensions of Money
- What Bitcoin Does
- How Bitcoin Works
- The Monetary Properties of Bitcoin
How Bitcoin Works
Bitcoin can send transactions and incorporate them into a public blockchain which serves as a ledger. Bitcoin is valuable because we can be certain the transactions included in the ledger are legitimate and not fraudulent. We can be certain they are not fraudulent because of the size of the Bitcoin network. This chapter will explain how the decentralized network incentivizes independent participants to organize and create legitimate transactions on the blockchain.
Decentralized Software
A computer is made up of memory and processing power. Memory is stored information that some computers have more of than others. Processing power is the ability to convert inputs into outputs and some computers can process faster than others. Software comprises rules that a computer is told to follow. A computer takes in inputs, applies the rules it is given, and produces outputs.
Bitcoin is software, but its nature is different from what we are used to because it is decentralized. Most software we are familiar with uses a centralized network to function. Consider Facebook and how it works. When you log in to create an account your information is uploaded to one of the many computers Facebook uses for storing the information of its users. Every time you make a post or comment that information is added to the computer. If the CEO wanted to delete or change your information then he would call the guy who manages the computers, give him your name, and tell him what to do with it. This is all possible because Facebook is a centralized company.
Indeed, most companies we are familiar with operate in a centralized manner and for good reason. The fact that the CEO is a phone call away from making these changes allows the company to function efficiently. In return for this efficiency, the stakeholders of the company (employees, shareholders, and customers) must trust that the CEO is doing what is best for all of them simultaneously. Roughly speaking, the CEO of a company does not require a consensus of agreement from the stakeholders to enact change, and this allows a company to be agile in a competitive market.
At the other end of the spectrum is a decentralized group – where decisions are made by achieving consensus among a group of participants. In its purest form this system does not require trust in a central authority because the will of the stakeholders will always be achieved. This process is inefficient but necessary for enacting operations that are highly subject to moral hazard.
America’s founding fathers knew this when constructing the balance of powers and our democratic process for electing officials. It allowed society to maintain a high degree of control over those whom they elect to be in charge. Put simply, purely decentralized systems are slow and inefficient, but necessary to eliminate the agency problem where a conflict of interest exists.
The age of computing enabled decentralized systems because the ability to transfer information at near the speed of light made the requirements of decentralization much less onerous. Software became the ideal medium for decentralization. With computing advances came a new universe of ideas that could now be decentralized, but remain operationally feasible.
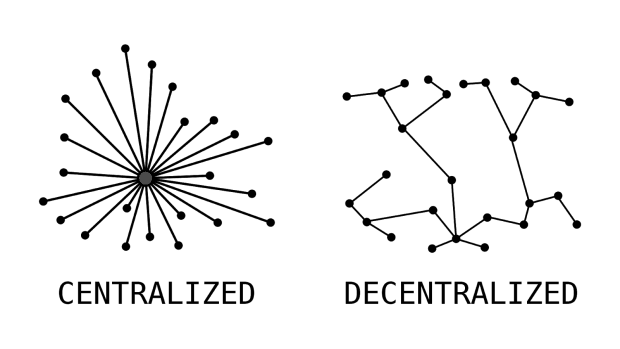
Decentralized software is code that is automated enough so that there does not need to be a centralized owner (like a CEO). Instead, it is a set of rules that everyone who interacts with the software is required to follow. Once the rules are set they cannot be changed, UNLESS most network participants agree to make the change.
This agreement is achieved through action because the software is open source – everyone has their own copy of the code which they can change in whatever way they wish. However, if one changes their code too much, they might not be able to interact with other people’s code anymore. Everyone can change their own code however much they would like, but the rules that are followed are those that most of the network chooses to follow. Anybody that does not want to follow them can change their code, but this means that they can only interact with others who have made this change as well. Simply put, if somebody wants to change the Bitcoin software, then they need to convince the majority of participants to do the same. If they cannot, Bitcoin will not change.
Decentralized systems follow a set of rules. The rules change when the majority of participants download software with the rule change. If they do not, the rules remain, and the minority must decide whether to stay or leave.
The Bitcoin Network
The Bitcoin Network exists as the sum of all network participants. Participants are called nodes – a computer with compatible Bitcoin software connected to a network. Each node in the network can participate in multiple ways, depending on the software it uses, and is constrained by its memory and processing power. There are currently approximately 10,000 Bitcoin known nodes worldwide, as seen on the map below:
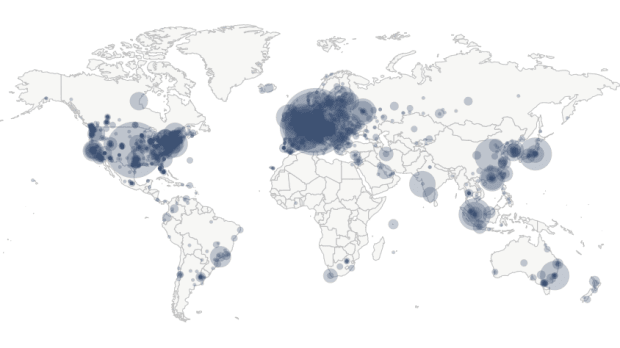
Nodes participate in the network via three primary functions: routing, verification, and mining. When a node hears about a transaction it verifies it by checking that the sender has enough bitcoin to spend, that they haven’t spent those bitcoins anywhere else, and that their signature matches their address. If all checks are successful the node routes the transaction to other nodes, but if not, it forgets about it. Mining nodes not only verify and route, but they also add transactions to their memory pools and attempt to record their memory pool copy in the blockchain by solving a computational puzzle (proof of work).
The Mining Process
For a new block to be mined and included in the blockchain, a mining node must solve the proof-of-work (PoW) computational puzzle. The proof-of-work algorithm is solved by generating a hash of the block header items that falls below the difficulty target. Because a hash function’s output is random, the only way to produce a low enough number is by guessing. The difficulty target is used to increase or decrease the chance that a miner solves the proof of work algorithm. The lower the difficulty target is, the harder it becomes to solve because the range of possible answers is smaller.
Recall the block header items from the prior essay:
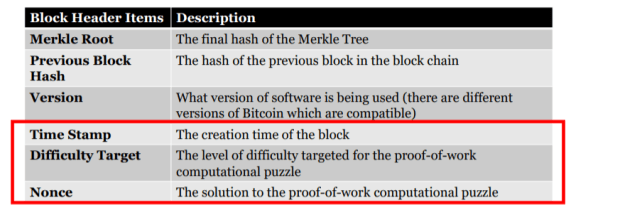
The below formula combines all of these items and hashes them to calculate the block header hash:
block header hash =
hash-function (merkle root + previous block hash + version + time stamp + difficulty target + nonce)
Miners can change what the block header hash is by changing what they put into the nonce field. So, if the block header hash is less than the target difficulty, the block is successfully mined. The reason you cannot just pick a low number is because the hash functions output is random (there is no way to just make it produce a low number).
Miners compete to solve the proof-of-work computational puzzle by iterating the nonce field until it produces a block header hash less than the difficulty target.
The Longest Chain Rule – Resolving Disagreements
Once a miner finds a solution, they immediately broadcast it to their peers (i.e., nodes which they are connected to). Those nodes then verify that the solution is correct and, if so, broadcast the solution to their peers. The chart below shows that 95% of the blockchain will become aware of it in about 40 seconds on average.
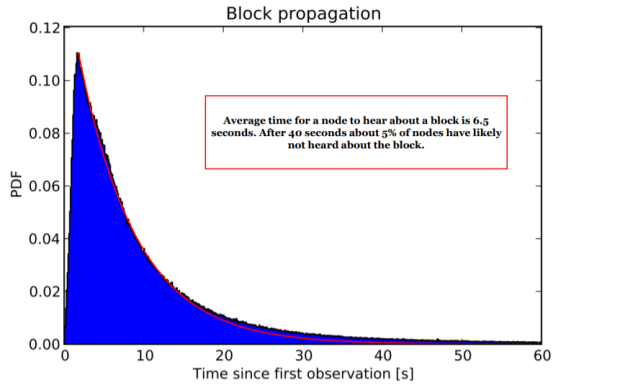
Nodes accept this new block by incorporating it into their copy of the blockchain. Miners accept this new block and begin mining the next block, with the newest block added to their blockchains, thus restarting the process. This cycle occurs on average every 10 minutes – the difficulty target automatically adjusts to make it so.
Because the difficulty target adjusts to find a block on average every 10 minutes, we know that a miner will receive a block reward every 10 minutes on average for successfully mining the block. The block reward includes the fees which nodes pay on a transaction, and the coinbase transaction creates more new bitcoin.
Block reward = coinbase transaction + block fees
The coinbase transaction rewarded 50 bitcoins in 2008 and is designed to cut in half every four years until the year 2140 when it will reach the maximum supply of 21 million bitcoin.
What if different copies of the blockchain from different nodes are solved simultaneously? If there are disagreements between nodes, they follow the longest chain rule:
- They work on the first block they receive but save the other branch of the blockchain in case it becomes longer.
- One chain will become longer once the next block is found, and the nodes of the shorter chain will switch to mining the longest chain.
Nodes follow the longest chain rule which resolves all disagreements over time.
Incentives – The Proof-of-Work (PoW) Algorithm
An important question to answer: why isn’t some miner’s block just randomly picked every 10 minutes? Why do we have to consume all this energy running computers to solve this problem?
Well, we know PoW creates digital scarcity but there is also another purpose – security. The blockchain is extended by those who solve the algorithm. If a miner solves it they could incorporate transactions that are fraudulent. However, these fraudulent transactions would be rejected by other nodes because they don’t pass verification. So, in order to extend the blockchain with fraudulent transactions, it would have to be extended by the miner who has the interest in doing so. This would require greater than 50% of the computing power of the entire network. So, the more expensive it is to mine, the harder it is for a bad actor to do so.
It would also not be in the bad actor’s best interests to do so. In Satoshi’s words:
He ought to find it more profitable to play by the rules, such rules that favor him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.1
In other words, if someone successfully attacked Bitcoin it would simultaneously destroy the value of bitcoin (because the network is no longer secure, so nobody would want bitcoin) and the attack would be worthless. This game-theoretic incentive is a major defense of Bitcoin against bad actors.
The proof-of-work algorithm is like a test. Much time and energy has been spent by students to take tests that produce nothing of tangible value other than proof of their knowledge. By doing so, schools gain credibility from the performance of their graduates and feel comfortable graduating them because they have proven their knowledge.
Similarly, Bitcoin gains credibility by the security of its network. Its security is in the fact that people know with certainty there will only ever be 21 million bitcoin. The cost of mining is what makes this certain. Securing the Bitcoin network means securing a trustless, decentralized monetary medium that is not subject to moral hazard. A monetary system is the foundation of an economy, and in turn its security is of the utmost importance. Fiat money is more like a school without tests.
The Rules Of Bitcoin
With an understanding of what Bitcoin does and how it works we can now summarize the most salient rules that nodes of the Bitcoin network follow. Bitcoin is software, so if you want to know the rules the best way to do that is to review the code. If you don’t know how to do that, below is a summary of the most salient rules. These rules are necessary to grasp how Bitcoin’s software forms transactions, compiles them into blocks, secures the blocks into a chain, and secures a fixed supply schedule of new bitcoins. Below the rules are delineated between the transaction level and block level for ease of understanding, although some rules are not mutually exclusive and could be included in either category.
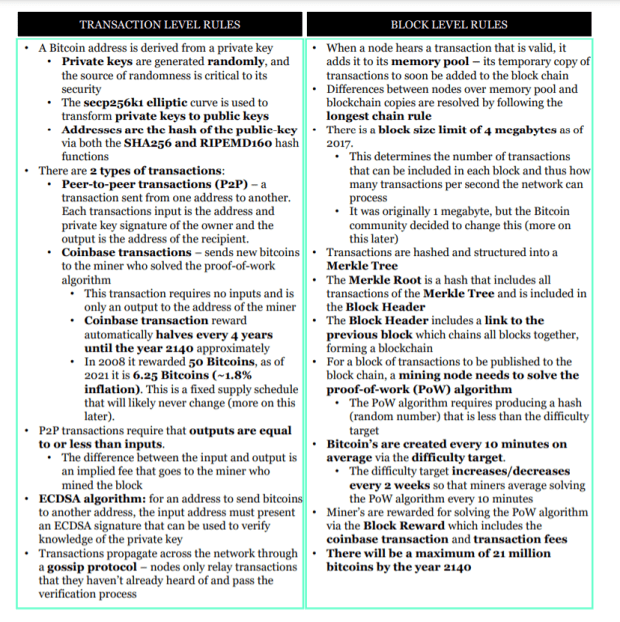
These rules exist from consensus as network participants willingly accept them. Participants accept them by downloading the Bitcoin software and utilizing it. In fiat systems, rules do not emerge by consensus but by decree (the definition of the word fiat). We do not vote on our monetary policy. Rather, monetary policy is influenced by politicians and controlled by these people:

Why Bitcoin Is So Valuable.
People buy bitcoin because of its superior money properties, increasing its price. Price increases attract more miners, expanding the computing power of the network, and making the network more secure and thus more valuable. This further increases the price over time. As the bitcoin price rises it creates a positive feedback loop in which participants believe it will continue to rise. That is the power of a network effect when applied to a standard of value. This feedback loop is predicated on Bitcoin’s monetary properties (determined by the rules) because people would not have speculated on bitcoin in the first place without them. The monetary properties of bitcoin will be covered in the next essay.
How The Rules Can Change
The Bitcoin software is called Bitcoin Core which can be downloaded at bitcoin.org. This is the most widely used Bitcoin software, but there are other valid versions of the Bitcoin software. The other versions must maintain a minimum level of similarity with Bitcoin Core to participate in the Bitcoin network. This minimum level is that a node needs to check for the validity of transactions and blocks in the same way as other nodes. If it does not, the transactions/blocks it creates and relays will likely not be accepted by other nodes and vice versa. Bitcoin Core is the standard of these rules and thus, the de facto rulebook of Bitcoin.
In order for the rules to change consensus needs to be achieved across the three primary stakeholder groups:
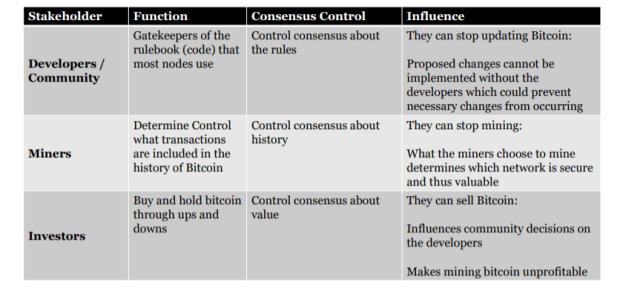
You can see that each group has a form of power, but none have full control. Note that there is a small group of developers that can actually update the code (called commit access) while the rest of the community publicly propose changes.
What if somebody attempted to control this small group of developers with commit access? Well, they have the power to make new software for the community to willingly download but cannot make them download it. Further, all changes to the software are reviewed by community members because it is open source, therefore any changes are quickly identified.
The Bitcoin rules are created by the community and implemented by developers with commit access. Nodes (miners) must download the updated software for the network to accept it and investors must continue to hold and buy bitcoins for the software change to matter.
Changes to the rules of Bitcoin require consensus across the the primary stakeholder groups.
Our fiat financial system is controlled by a highly centralized group. You have a choice of whether you want to abide by the democracy of the Bitcoin system or the continuously changing rules of the present fiat system. As more people adopt the Bitcoin system, this decision will become much easier. However, this adoption will require significant development of the current ecosystem that supports it, covered in the next essay.
References
- Bitcoin and Cryptocurrency Technologies, Arvind Narayanan, Joseph Bonneau, Edward Felten, Andrew Miller, Steven Goldfeder, 195
Eric Yakes came from the private equity industry and is a CFA charterholder turned bitcoin pleb and author of The 7th Property: Bitcoin and the Monetary Revolution – a comprehensive/technical resource on money, banking, and bitcoin. He is passionate about enabling the Bitcoin ecosystem through financial services – if you have similar interests send him a DM @ericyakes.
This is a guest post by Eric Yakes. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.