DeFi Protocol bZx Hacked Again: $8 Million Worth of ETH, LINK, Stablecoins Drained
In yet another jolt to the decentralized finance (DeFi) community, margin, and leverage-based lending and trading platform, bZx became the target of another hack. In the hack, which was much bigger than the previous attacks, hackers made away with $8 million worth of cryptocurrencies.
bZx Hackers Deal 8 Times More Damage To The DeFi Protocol This Time
DeFi lending protocol bZx was attacked again. This time hackers drained a little more over $8 million worth of cryptocurrencies leveraging a duplication bug that enabled them to make away with 219,199.66 LINK, 4,502.70 ETH, 1,756,351.27 USDT, 1,412,048.48 USDC, 667,988.62 DAI.
bZx team member Anton Bukov shared a thread on Twitter, in which he admitted that a faulty line of code in the smart contract led to hackers initiating a series of iToken duplicating transactions to steal ETH:
We realized that initial source code works incorrectly when “_from” equals to “_to” and leads to funds duplication. We found 9 exploiting transactions on $iETH lending token with 101778 $iETH tokens duplicated (worth ~4.7K $ETH) // @DuneAnalytics pic.twitter.com/IWodBkGaEq
— Anton Bukov | k06a.eth (@k06a) September 13, 2020
How Did It Happen Exactly?
On delving deeper, bZx’s official incident report reveals that a loophole in the ‘transferFrom() function’ that enables the transfer of ERC20 tokens from one protocol to the other was leveraged by hackers.
It was possible to call this function to create and transfer an iToken to yourself, allowing you to artificially increase your balance.
To be precise:
- Attackers invoked a transfer function with the same _from and _to address of the original function.
- Then they immediately called an ‘_internalTransferFrom’ function with the same set of arguments, making the below lines of code faulty.
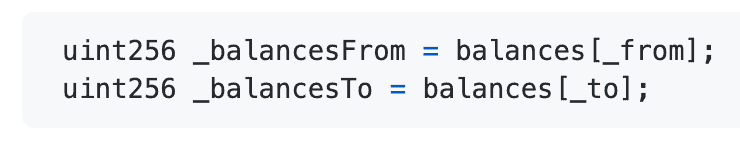
This resulted in _balancesFrom _balancesTo being equal.
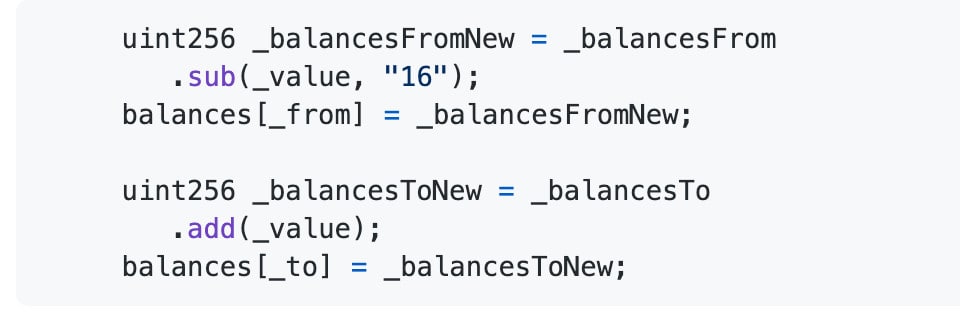
This, in turn, enabled the attackers to ‘decrease the balance of _balancesFrom and increases the balance of _balancesTo’. As per the report:
The user was effectively able to increase his balance artificially.
bZx patched the faulty code after the $8 million theft. The fix has set the ‘move of balancesTo being set after the deduction from balances[_from]’ effectively preventing anyone from artificially inflating their balance.

The leading DeFi lending protocol went ahead and applied the patch after code auditing firms Certik and Peckshield gave the green light.
Not The First Attack on bZx
It seems this year is not turning out to be a good one for bZx. As CryptoPotato reported, earlier in the month of February, a hacker dealt two consecutive blows and stole a combined $1 million in ETH.
In the first one that happened on February 14, the attacker used different methods in both the attacks. In the first one, he/she borrowed 10,000 ETH from dYdX. Out of the 10,000ETH, 5,500 ETH was used to collateralize a loan for 112 wBTC on Compound.
Then the online robber spent 1,300 ETH to open a 5x leveraged ETH/BTC short position on bZx’s Fulcrum trading platform, while also borrowing 5,637 ETH through Kyber’s. He/she swapped this amount for 51 wBTC, causing a serious slippage.
By swapping the 112 wBTC from Compound to 6,671 ETH and the hacker made a profit of 1,193 ETH, amounting to around $318,000 (considering the prices then).
The second one that took place on February 18 saw the attacker leverage ‘oracle manipulation’ to game the system and drain around $600,000.
The post DeFi Protocol bZx Hacked Again: $8 Million Worth of ETH, LINK, Stablecoins Drained appeared first on CryptoPotato.