Chainalysis: Watching Those Who Are Watching Us
A recent event by blockchain surveillance firm Chainalysis explained how its tools are used and raised questions about whether they should be.
Blockchain analysis firm Chainalysis recently held the one-day “Chainalysis Links” conference with a variety of speakers, from former members of MI6, the police force, financial institutions and the United Kingdom’s HM Treasury to internal Chainalysis speakers and moderators.
The conference did not offer a lot of details on Chainalysis’ products or methods for surveilling activity on blockchains like Bitcoin’s, but it offered a high-level look at the context, uses and potential future of its various services and products, giving Bitcoiners a glimpse into those who are watching them.
The Chainalysis Business
As one aspect of its business, Chainalysis provides market data on some insightful metrics measuring Bitcoin activity. This included information on cryptocurrency-based hacks, information on the use of Bitcoin for child pornography, Bitcoin adoption metrics and its uses in criminal activity.
Another service Chainalysis offers is aiding companies in complying with government recommendations via a service that does real-time analysis of blockchains.
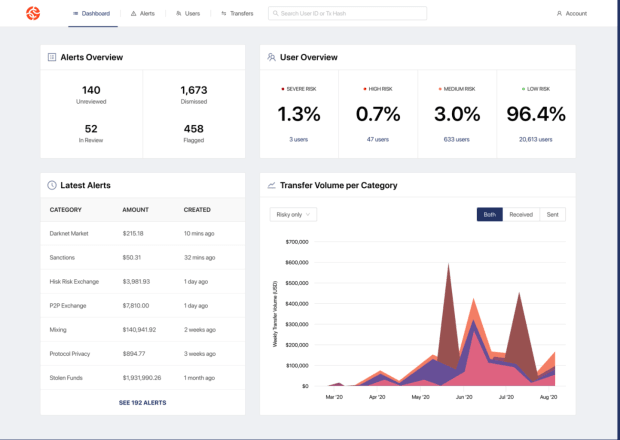
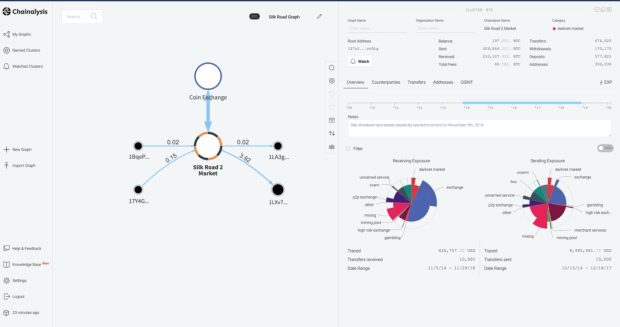
A third area is in transaction tracking and investigation, with a tool called KYT and a tool called Reactor, which are both used for investigations on Bitcoin and other blockchains.
In case you’re wondering what these platforms look like, here are a couple screens from the public website:
As a sidenote on the Chainalysis business, it recently purchased and put bitcoin on its balance sheet. But, as Bitcoin Magazine’s Namcios wrote, “the company doesn’t align very well to the true Bitcoin ethos as its business model is based on surveillance, allowing its customers to obtain information on bitcoin transactions for discrimination purposes.”
Definitions And Client Considerations
Given Chainalysis’ business lines and its ability to disrupt the pseudonymity Bitcoin is meant to provide, I went to the conference with questions about three main areas:
- What is the Chainalysis definition of “crime”? Within crime, how does it define categories like terrorism, illegal products and subverting democracy?
- What customers does it sell its investigative platform to, and who won’t it sell to or work with?
- How do its products work in detail?
With regards to the first question, an answer provided to a chat question during the conference stated that Chainalysis’ role is to produce a tool to be used in investigations. The firm is not a law enforcement agency.
Secondly, when asked if Chanalysis has criteria for entities it will not sell its products to, it responded that the criterion is “usually” whether or not the country or other client is sanctioned.
I reached out to Chainalysis to get a confirmation statement about these conference chat responses, but did not hear back from them.
During the conference, various people talked about use cases for the investigative platforms KYT and Reactor. These included:
- MI6 investigations of those suspected of subverting democracy or child abuse
- A specific U.K. investigation around firearms bought on the darknet
- An investigation of stolen cryptocurrency laundered via debit card use
The conference did not get into much specific or under-the-hood details about any products.
But the above use cases raise questions about the use of Chainalysis tools and tactics in the hands of “bad actors,” where the target of the investigation could very well be considered the “good guy.” To mirror the stated use cases with more complicated bad guy/good guy scenarios:
- What if the investigator is a dictator and the target is someone opposing that dictator?
- What if this is an investigation by a dictator or authoritarian regime purging or rounding up minorities, and they are looking to defend themselves by purchasing arms or other banned security mechanisms?
- What if the bad actor country or leader was using the financial tracking against an oppressed person or group of people to determine where and what they purchase?
All of these cases could also occur for smaller entities, like an organization or an individual.
Can Chainalysis Be Hacked?
One main tactic that Chainalysis is used for is tracking ransomware payments and money movement. Below is a Chainalysis Reactor graph showing the money laundering process for five of Evil Corp’s ransomware strains (yes, that’s the listed company name).
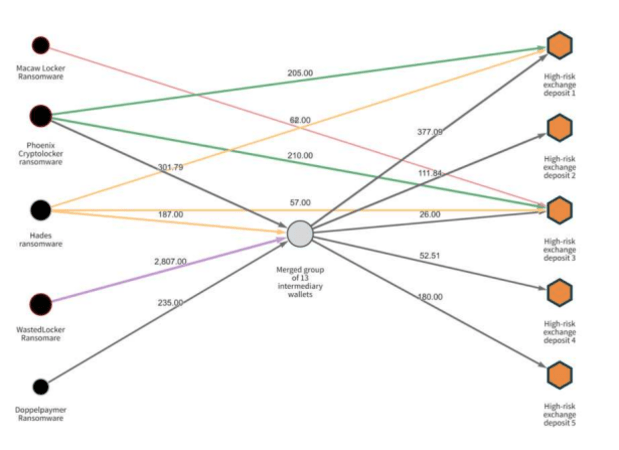
(Per the image above, you can also look at some info of how the Colonial Pipeline ransomware payment was tracked.)
If Chainalysis tools are sometimes used to track down ransomware companies’ money, these companies may be motivated to attack the platform. If you think about all of the information that is being aggregated for subjectively good or bad purposes, what happens if Chainalysis is hacked?
In that case, the information it obtains could be ransomed. That would affect everyone’s privacy.
Chainalysis Products, Use Of Dust And Behavioral Alerts
One of the questions that has come up around Chainalysis is whether its products use Bitcoin dust (microscopic transactions below the minimum limit) to correlate recipient addresses. Jameson Lopp wrote recently that he believes that Chainalysis does not use dust in this way, based partly on its below statement and the cost benefits of doing so, per a CoinDesk article:
“CoinDesk reached out to Chainalysis and CipherTrace to ask if they use dust in their analytics. Both companies denied using this technique, though Chainalysis Manager of Investigation Justin Maile added that dusting is ‘more often [used] by investigators’ to trace illicit funds. Maile continued that exchanges may use dusting to trace stolen funds following a hack.”
Chainalysis also has webinars about its “Behavioral Alerts” service, and how you can set them up.

In the webinar, the presenter noted that most illicit actors are aware of the standard behavioral alerts, and make their transactions with thresholds and timing to avoid those alerts.
But how many typical blockchain users know what rules will put them on the alert list?
There seems to be a non-zero possibility of good or benign actors getting caught in this analysis. Colin Harper wrote about this issue (with regards to mixing specifically) in a previous Bitcoin Magazine article, “The Bitcoin Mixing Case At The Center Of The Fight For Transaction Privacy”:
“Honest, privacy-savvy Bitcoin users should have nothing to worry about legally, so long as they have nothing to hide, Jesse Spiro, head of policy at Chainalysis, told Bitcoin Magazine… But Spiro’s comment betrays the consequence of this surveillance: Honest users can get caught in the crossfire.”
Future Directions: Automation Of Flags And False Positives
If you’ve ever encountered a positive-outcome vending machine malfunction, you’ve come upon the upside of an error and automation of that error — the machine continues to dispense snacks for free. (Yes, I know, Bitcoiners don’t eat that stuff).
As another example, anyone with a credit card has seen the number of false positives with regards to fraud. When you automate anything, if the methodology is imperfect, you can then automate errors at a more efficient and faster rate.
To make the platform more efficient and able to handle a higher number of smaller cases, many sessions talked about automating the data analysis and flagging of issues.
For false positives with a bank or credit card, the issue is a minor inconvenience. However, being falsely flagged for nefarious activity within other systems can put you under the wheels of that system and it can be difficult to prove innocence and extricate oneself. The systems mentioned included organizations such as the U.S. Internal Revenue Service, police and international crime units and banking systems worldwide.
It was noted during the conference that input from more data systems are going to be sourced, aggregated and otherwise used within the Chainalysis platform. It is yet to be seen what that will mean for generating false positives around what the platform deems to be “criminal” activity using platforms like Bitcoin.
Chainalysis, Privacy And Censorship-Resistance
In 2019, Chainalysis made a public statement of its privacy policy in response to public scrutiny around the privacy implications of deanonymizing blockchain transitions. If you don’t have financial privacy, you are not censorship resistant. Bitcoin is not censorship-resistant without privacy.
This is at the heart of the concern around the Chainalysis tools and its ability to do financial surveillance.
Chainalysis provides useful metrics that counteract false narratives. These include data on how much cryptocurrency is really used for “criminal” activities and data about cryptocurrency adoption by country and demographics.
However, the Chainalysis investigative analysis tools that are used against what most would view as “bad actors” can also easily be used against anyone. Its tools could also be used to suppress rights and freedoms where certain or arbitrary laws do not enable those rights and freedoms.
As world entropy increases, the greater good would be served if Chainalysis were to develop protocols regarding who it will sell their products to and what its definition of “crime” is in order to reduce the likelihood that they cause harm unintentionally.
Chainalysis may be enabling others to surveil the blockchains for nefarious actors. But privacy experts and Bitcoin plebs should also be watching and surveilling Chainalysis for similarly bad actors and actions.
This is a guest post by Heidi Porter. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.